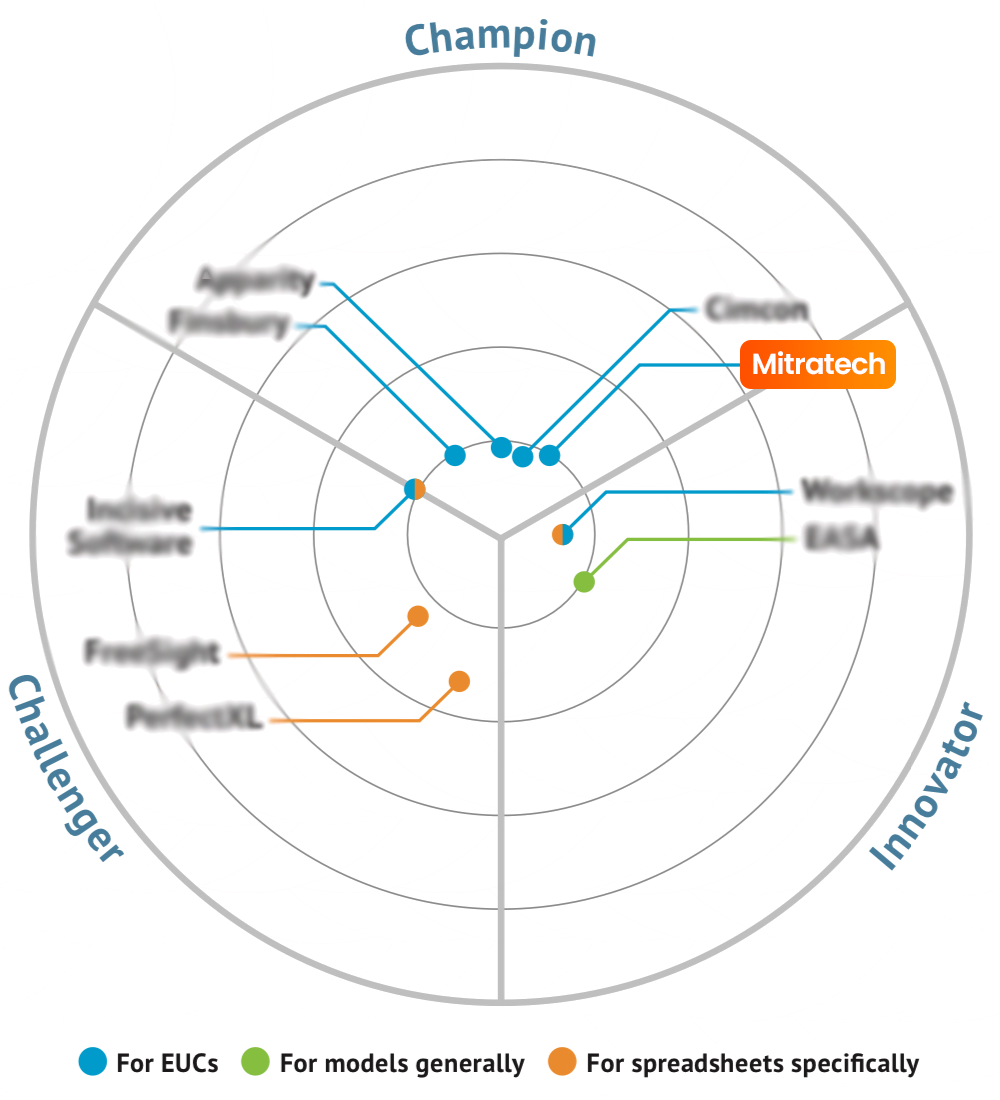
In an era of evolving End-User Computing (EUC) risk, explore the key features that earned Mitratech’s award-winning Shadow IT manager, ClusterSeven, a Gold Mutable Award in the 2023 Bloor InBrief Report.
For as long as Excel® Spreadsheets and Access® databases have existed, End-User Computing risk has been a concern for organizations worldwide. Luckily, as the scope and sophistication of these risks continue to evolve, as does the software designed to combat them.
Highlighting the top-forming EUC management and governance platforms is the aim of the 2023 Bloor InBrief Report, a free market analysis published by the independent technology analysts at Bloor Research. Before we dive into why Mitratech’s ClusterSeven was recognized amongst market champions with a Gold Mutable Award for features like comprehensive inventory, seamless risk assessments, robust controls, and so much more, let’s first unpack the latest industry knowledge surrounding end-user Computing applications — and why Shadow IT is a topic that should be on your company’s radar over the next few months.
First Thing’s First: What is End-User Computing (EUC) — and Its Associated Risks?
End-User Computing refers to any application developed or managed by end users rather than an IT department or professional software engineering team (think of platforms like Microsoft Excel®). They are especially prevalent in industries where end-users need to be able to manage and manipulate data efficiently or keep up with shifting regulations, like financial operations.
And as you might imagine, any software that leaves system-based processes in the hands of an average user — and falls outside of the purview of IT’s formal testing process — can pose risk, including regulatory fines, reputational damage, remediation costs, and more. And while some IT departments encourage this democratization of applications to help alleviate workload and elevate efficiency, any organization where these EUCs are not properly governed is leaving itself exposed. Even more concerning, oftentimes the IT department won’t know about these unmanaged applications until it’s too late.
What is Shadow IT?
When an end user engages with any information technology systems, applications, software, or services without explicit IT department approval, they fall under the purview of Shadow IT. Did you know that the average enterprise contains 4-10 times as many Shadow IT applications as corporate-managed apps? That means that these risks are hiding in more places than you think (and aren’t subject to the same monitoring that traditional corporate applications allow).
A rise in EUC risk and its associated costs has sparked a need for a parallel increase in end-userComputing or Shadow IT Management, which includes an organization having a system in place that allows them to:
- Identify End-User Computing risk
- Define additional EUC controls needed to manage that risk
- Establish necessary reporting and monitoring processes for oversight
- Establish protocols for action in the case of rising risk levels or monitoring exposing exceptions
- Establish an appropriate response
Since a manual approach is often inefficient and troublesome, many organizations are taking a system-based approach to supporting their control frameworks. Tech-enabled EUC Management can help with the following use cases:
Enter: Mitratech’s ClusterSever and the 2023 Bloor InBrief Report.
Stay One Step Ahead of Shadow IT and EUC Management
The 2023 Bloor InBrief Report identifies the industry leaders and shapers in EUC management and governance based on the following 8 criteria:
-
- Inventory — Does the software offer a robust discovery process for EUC risk detection, and a comprehensive, up-to-date inventory for real-time monitoring?
- Risk Assessment — Can this platform deliver detailed risk assessment to support prioritization of governance, remediation, or application removal?
- Controls — Do you have the ability to configure your control based on the level of risk involved?
- Regulations — Do you have the data lineage capabilities and audit trail that you need to appease regulators and ensure compliance?
- Spreadsheets — Does the partner provide error and defect detection, spreadsheet comparisons, etc.?
- Architecture — Can you centralize EUC management in one database, and then report against that database?
- Automation — Does the platform offer automation to streamline data collection, reporting, and more? (Mitratech’s ClusterSeven was a standout in this regard).
- Ease of Use — Does the software offer the intuitive capabilities needed to help the end user to do their job effectively, while working in the background to ensure security and compliance?
Interested in learning more about ClusterSeven’s feature in this year’s report? Download the excerpt for a closer look at:
- A visual representation of ClusterSeven’s “lifecycle” approach to delivering EUC governance and MRM in a continuous and ongoing fashion
- A detailed breakdown of how the platform helps you find, understand, manage, and monitor EUC apps and assets that currently reside under the banner of shadow IT
- A closer look at the ClusterSeven capabilities across discovery, inventory management, active monitoring, and reporting that earned it recognition in this InBrief Report
Explore Award-Winning Shadow IT and EUC Management
See Why ClusterSeven Won a Gold Mutable Award in the 2023 Bloor InBrief Report