Phishing Preparedness: What Does a Risk Manager Recommend?
Carly Franks, Senior IT Security Risk & Compliance Analyst at Mitratech, has more good guidance to offer on the subject of phishing, so your employees can stymie the fraudsters out to purloin personal data.
The gentleman in the image above just realized there was something not-quite-kosher about that email he just opened, purportedly from his own CEO, or CFO, or someone else claiming to be a trustworthy correspondent. During the pandemic, these bad guys had less shame than ever and upped the frequency and ingenuity of their attacks.
As the Oxford English Dictionary defines phishing…
noun; the fraudulent practice of sending emails purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers; “an email that is likely a phishing scam.”
There are too many different phishing subspecies to get into here. That’s what Wikipedia or a sobering conversation with a compliance officer or email administrator is for. We’d like to focus on how to spot a phishing attack and the measures an employee should take to verify the authenticity of a suspect email.
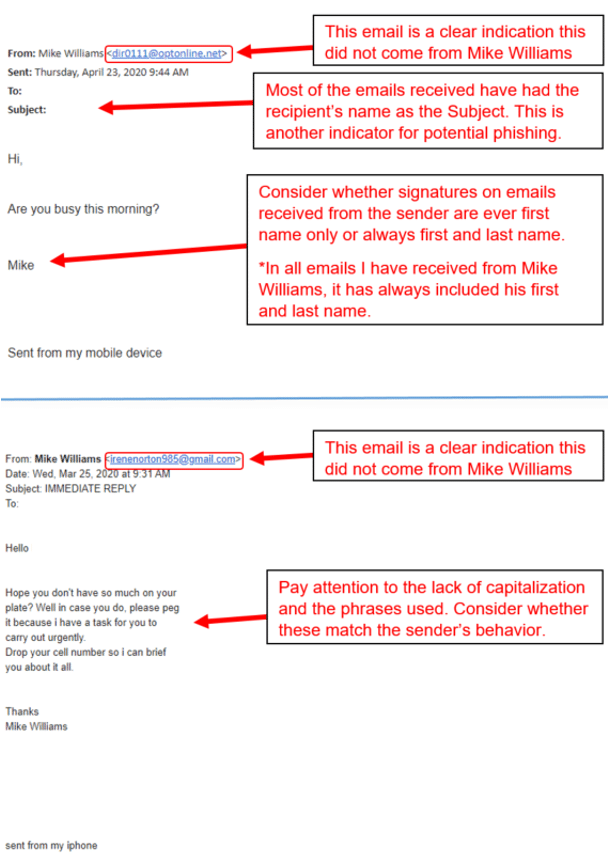
Carly has a terrific example to share: A phishing attempt that was carried out using the name of our own CEO at Mitratech, Mike Williams, as the bait.
Being on guard against “familiar” names
In this case, Carly points out the phishing indicators from a few of the emails that were supposedly coming from Mike Williams. Notice in both of the examples below how the sender’s email is the first clear indication this is not coming from Mike.
As a reminder, here are five keys for recognizing and protecting yourself from phishing emails:
1 • Look at the actual email address of the sender, not just the display name, as well as the timestamp of when the email was sent. Make sure the email address is the correct email of the sender and the timestamp fits the sender’s behavior. If you received an email at 1:30 AM from a sender that never works outside of normal hours, be suspicious.
2 • Be aware of spelling and grammatical errors. Understand there is a difference between language barriers and spelling and grammatical errors. Do not dismiss something due to English not being the native language of the sender. But if your sender doesn’t tend to make errors, make that your first red flag. These can include:
- Use of punctuation, or no punctuation at all. Does the sender typically use proper punctuation?
- Lack of proper use of case.
- Misspelled words. Does the sender typically misspell common words? Does the spelling of words match the language of the sender?
Below is an example of a phishing email that claims to be from Microsoft Skype, but has a few telltale clues that it’s a fake.
3 • Never open or download an unknown attachment. If you are not expecting an email, much less an attachment, assume it’s a phishing email until you have verified it with the sender.
4 • Never click on links in emails. All of us inside companies receive internal emails all the time with links to internal resources; however, get in the habit of never clicking on links. Instead, right-click on the link (email, unsubscribe option, hyperlink, etc.), select copy (copy email address, copy link address, etc.), then paste into the appropriate field (new email, web browser, etc.). Doing this will help prevent you from being redirected to a malicious site and compromising your username and password or sensitive information.
5 • Be alert to urgency. If you receive an email that requires urgent action, stop! Evaluate it, look for any items identified above, determine if urgency is warranted, then take appropriate action. Urgency is one of the top methods used to get the recipient to take down their guard. Often the timing of phishing emails (e.g. late in the afternoon) and the urgency they demand are key red flags.
How to verify an email?
Never verify the legitimacy of an email or its contents by replying to the original sender. Also, do not verify using any of the contact information provided in the email. Instead, do the following:
- Call the sender to verify the email and its contents.
- Send a separate email to the known email address of the sender to verify the legitimacy of the suspect email before taking any action on it.
- If the sender is a fellow employee and uses a common chat tool like Slack or Teams, send them a message using that tool to verify they’ve send you the email.
As the handy acronym tells us, S.I.T. on the email until you’re sure it’s trustworthy. Stop, Identify if any of the phishing indicators are present, and Take action by verifying the email and deleting any that aren’t legit.
Other measures to remember?
- If you think you’ve been taken in by a phishing email, be sure to report it immediately to your IT and/or data security team.
- Not sure it’s a phishing attack? Check with those teams. Or your company may have a posted guide or channel where you can get information, including updates on the most recent scams.
Nowadays, you can’t be too careful, unfortunately. Or as Carly Franks tells us,