What Is End User Computing (EUC) Risk?
A guest post by Sam Lee, Head of Operational Risk, EMEA, SMBC, Torchlight Services
End User Computing is a system in which users are able to create working applications besides the divided development process of design, build, test and release that is typically followed by software engineers. Microsoft Excel is perhaps one of the best known examples of an EUC platform.
With that in mind, EUC risk is therefore the potential for errors in key EUC business documents like spreadsheets. The flexibility of EUCs can lead to faults being made in these critical company documents. Given that the data produced by EUCs is generally accepted and relied on by management and other end users, this can quickly lead to incorrect data and, in turn, increases the risk of financial and reputational loss.
Why is EUC risk important?
While EUC risk is universal, it isn’t as well known or perhaps even recognized as some other enterprise risks, such as operational, financial and regulatory (or their sub categories). “Why do I need to care about EUC risk?” is often asked. There are two reasons.
Foremost, EUC risk is present in any organization that relies on spreadsheets, databases and other ‘man-made’ computing tools that sit outside of the IT application cycle. The level of the risk is informed by the risk management framework in the organization, but it is unlikely that a business does not use the above mentioned applications.
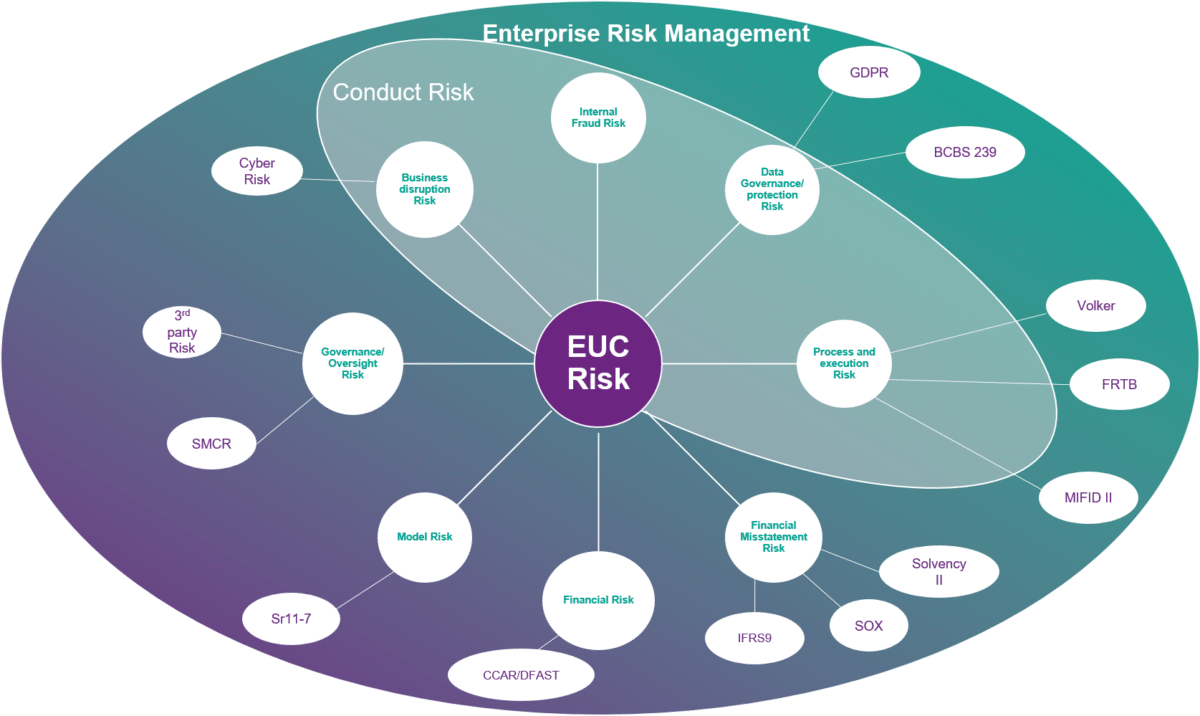
Secondly, EUC risk contributes to a whole host of other operational, regulatory and conduct risks. There’s a great deal of intercoonnectivity between EUC and other risks – all of which cumulatively contribute to enterprise risk. The diagram below shows this very clearly.
Therefore, one should challenge any organization that argues that EUC risk is not relevant to it in some shape or form. It’s imperative that organizations get to grips with the meaning of EUC risk.
The good news is that it is possible to manage and control End User Computing risk, even though it is fundamentally present across an organization. So, where’s the logical place to start?
End User Computing risk is an often underestimated threat, with data from EUCs providing the foundation for critical business decisions and reporting. Here are some top tips for managing your EUC risk:
 Understand the EUC population in your organization – the types of EUC applications used; how many there are of each type; and what is the level of complexity , or inherent riskiness of the different files – i.e. which ones are heavily coded, use macros, rely on connections to other spreadsheets, databases, etc.
Understand the EUC population in your organization – the types of EUC applications used; how many there are of each type; and what is the level of complexity , or inherent riskiness of the different files – i.e. which ones are heavily coded, use macros, rely on connections to other spreadsheets, databases, etc.
 Determine the ‘criticality’ of the EUCs to the business. Criticality must be assessed based on the quantitative (dollar loss) and qualitative (reputational risk, client exposure, regulatory sanction, loss of business functionality) impact on the business if these files were lost or otherwise unknowingly damaged or altered. For instance, assess what the cost to the business would be if the creator of a vital spreadsheet application left the organization? Would another member of the team have intimate knowledge of how the application works and needs to be maintained? Would they be able to test the integrity of the application in the event of inadvertent or malicious changes to any codes or macros in the application?
Determine the ‘criticality’ of the EUCs to the business. Criticality must be assessed based on the quantitative (dollar loss) and qualitative (reputational risk, client exposure, regulatory sanction, loss of business functionality) impact on the business if these files were lost or otherwise unknowingly damaged or altered. For instance, assess what the cost to the business would be if the creator of a vital spreadsheet application left the organization? Would another member of the team have intimate knowledge of how the application works and needs to be maintained? Would they be able to test the integrity of the application in the event of inadvertent or malicious changes to any codes or macros in the application?
 Design a policy for the creation of an EUC inventory, including definitions for the various levels of risk and the associated controls that must be put in place based on the criticality of the files. Additionally, the policy must also include rules for documenting, testing and maintaining the inventory of EUCs based on their criticality categorization. Obviously, the higher the criticality, the tighter the rules and more stringent the policies.
Design a policy for the creation of an EUC inventory, including definitions for the various levels of risk and the associated controls that must be put in place based on the criticality of the files. Additionally, the policy must also include rules for documenting, testing and maintaining the inventory of EUCs based on their criticality categorization. Obviously, the higher the criticality, the tighter the rules and more stringent the policies.
 Create a heat map of critical EUCs and using Key Risk Indicators, show where the delinquent EUCs are. This representation will help the organization take corrective action.
Create a heat map of critical EUCs and using Key Risk Indicators, show where the delinquent EUCs are. This representation will help the organization take corrective action.
 Focus on the most critical EUCs, understand their use and map them to the potential wider risks as identified in the organization’s risk library. For instance, assess if any of the spreadsheet applications impact other risks such as internal fraud, financial reporting, data governance and so on.
Focus on the most critical EUCs, understand their use and map them to the potential wider risks as identified in the organization’s risk library. For instance, assess if any of the spreadsheet applications impact other risks such as internal fraud, financial reporting, data governance and so on.
Undertaking this kind of end-to-end and granular approach manually is almost impossible, due to the extent of spreadsheet and EUC usage in most organizations. Not only is it difficult to holistically identify and inventory the EUCs, it is also challenging to determine the inter-connections and corresponding impact of critical spreadsheets on other enterprise risks.
It is also almost impossible to effectively track changes to code, macros, and so on manually, whether the changes were deliberate and bona fide, or otherwise. Adopting technology that automates discovery, inventory, policy enforcement, control and overall management of the EUC landscape is the most cost-effective and fail-safe way forward.
Discover PolicyHub
It's the Policy Management solution that’s easy to use, so you can build stronger compliance.