The cyber attack on MGM Resorts: what you need to know (and what it means for your risk management strategy)
Just this week, global hospitality, casino, and entertainment company MGM Resorts reported a large-scale cyber attack that impacted its operating systems, causing downtime throughout its casino floors, reservation systems, booking systems, email systems, etc. Even the hotel’s electronic key card systems went down, locking many guests out of their rooms.
The attack breached a handful of MGM properties across the United States in addition to some of its most renowned casino properties in Las Vegas, like Mandalay Bay, the Cosmopolitan, and the Bellagio. And while the casino floors are back online, the company’s reservation and booking systems are still down more than a day after the initial report amid the ongoing incident.
But though this attack came as a surprise to many, was the writing on the wall? Can we expect this to be an isolated incident? Let’s dive in.
Inside the MGM cyber attack: what’s the Impact?
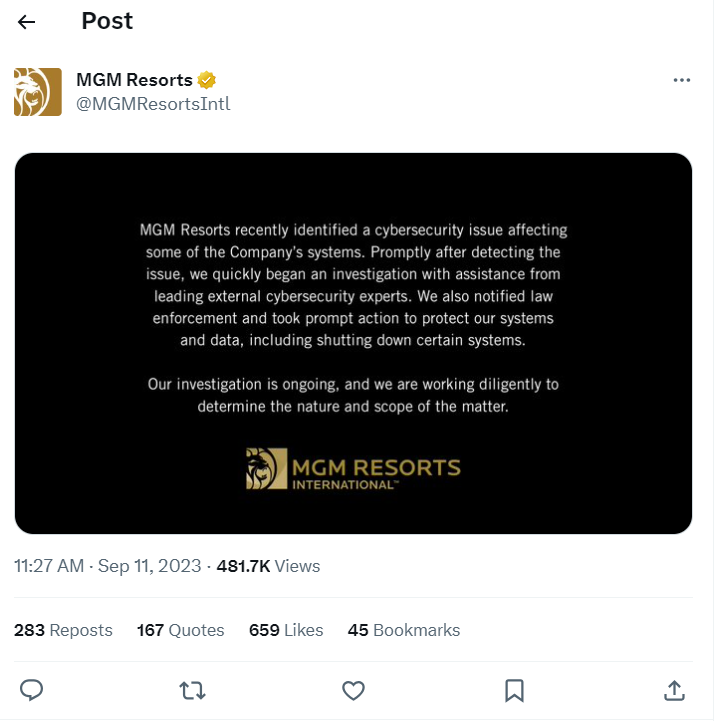
Since the first detection of the cyber attack on the evening of Sunday, September 10th, the organization has launched an investigation with assistance from leading external cybersecurity experts.
“We quickly began an investigation,” MGM reported Monday on X (formerly Twitter). “We also notified law enforcement and took prompt action to protect our systems and data, including shutting down certain systems.”
Allegedly, hackers used LinkedIn information to impersonate one employee to manipulate sensitive information out of another.
The FBI has reported that it is aware of the incident and that the investigation is ongoing. In the meantime, here’s a glimpse at the fallout:
- MGM’s website has been replaced by a temporary landing page advising visitors to contact their hotels or casinos directly by phone.
- MGM’s reservation and booking systems are still down
- MGM shares closed down nearly 2.4% on Monday
As demonstrated in this scenario, cyber attacks not only impact an organization’s downtime, but also have a direct, bottom-line impact on how investors and customers interact with your enterprise). That’s why — even amid tightening budgets and staffing challenges – it’s never been more important to align your cyber risk management roadmap with your organization core objectives (and bottom line). It’s also why organizations are turning to cloud-native, automation-driven technology (like Mitratech’s Alyne) to get on the fast-track towards better visibility and confidence for their stakeholders with continuous monitoring, quantifying, and reporting capabilities.
Cyber attacks on retail, hotels and hospitality – not a new concern, but an evolving one
This is not the first cybersecurity incident reported by MGM; just three years ago, in 2020, more than 10 million MGM visitors had their proprietary data leaked on a hacking forum. And other hotel chains have experienced the same frustrations. Dating back even further, hotel chain Marriott revealed a massive breach that exposed nearly half a billion customers’ data in 2018
And hospitality isn’t the only industry at risk from these attacks; IT Security Company NCC Group’s Monthly Threat Pulse of March 2023 recently reported a 91% increase in ransomware attacks in March 2023 compared to February 2023 and a 62% increase year over year when compared to data from March 2022.
The reality is: any organization or industry dealing with sensitive, proprietary data (which is…. nearly all of them) is at higher risk of suffering a cyber attack or breach in today’s cyber environment.
There remains a clear agility gap between today’s bad actors and an enterprise’s risk management system. As Bob Maley, CISO at Black Kite Technology, explained in a recent webinar (and our latest eBook), bad actors are more agile than organizations are at “observing, orienting, deciding, and acting.” Risk management, therefore, needs to become a process that’s always moving — and companies need to treat the idea of risk less as an isolated and unexpected incident that can occur at a singular point in time, but rather as part of the fabric of a continuous and constantly shifting environment that requires constant vigilance.
Bringing your risk management from reactive to resilient – and measuring it
To expand your risk strategy and make it a process that you can continuously and constantly improve upon (and measure), you’ll need to bring in more people from your organization, constantly sharing new information as it becomes available, and staying agile with automation-based technology.
The key to a successful risk management strategy involves a shift in mindset, where threats are no longer considered surprises, but instead, are expected events that affect every business. To navigate this change, strategic businesses employ risk management technologies that pair machine learning with constant vigilance to help users identify, mitigate, and report on risk.
Look for technology that can help you:
- Proactively identify and mitigate risk
- Continuously monitor
- Quantify risks via a built-in simulation engine
- Report on new risk patterns
- Leverage cyber risk assessments
- Align regulatory frameworks for compliance
- Extend practices to third parties
Elevate your GRC program today!
Reach out to our team with any questions, schedule a demo or learn more about Mitratech’s GRC solutions.